Azure Firewall Premium Preview in the Azure portal
Learn about Azure Firewall Premium Preview in the Azure portal.


Azure Firewall Premium is currently in public preview. This preview version is provided without a service level agreement, and it's not recommended for production workloads. Certain features might not be supported or might have constrained capabilities. For more information, see Supplemental Terms of Use for Microsoft Azure Previews.
Azure Firewall Premium Preview is a next generation firewall with capabilities that are required for highly sensitive and regulated environments.
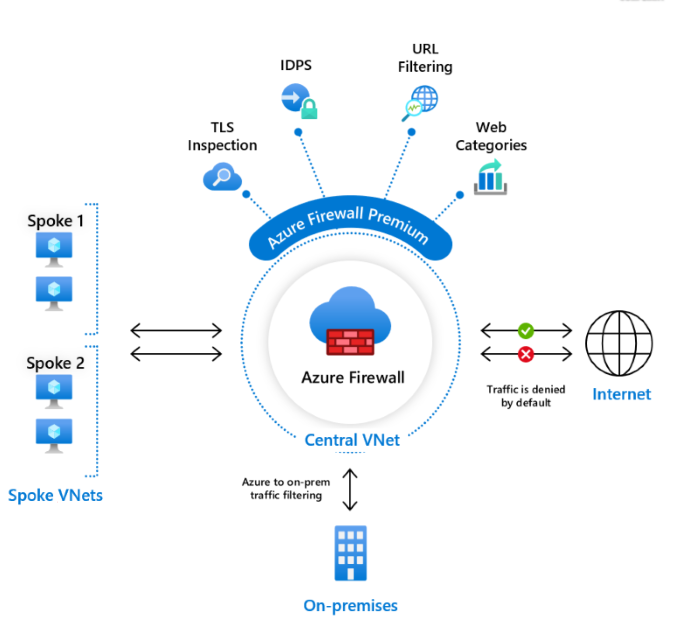
Azure Firewall Premium Preview uses Firewall Policy, a global resource that can be used to centrally manage your firewalls using Azure Firewall Manager. Starting this release, all new features are configurable via Firewall Policy only. Firewall Rules (classic) continue to be supported and can be used to configure existing Standard Firewall features. Firewall Policy can be managed independently or with Azure Firewall Manager. A firewall policy associated with a single firewall has no charge.
Currently the Firewall Premium SKU is not supported in Secure Hub deployments and forced tunnel configurations.
www.contoso.com/a/c instead of www.contoso.com.Azure Firewall Premium terminates outbound and east-west TLS connections. Inbound TLS inspection is supported with Azure Application Gateway allowing end-to-end encryption. Azure Firewall does the required value-added security functions and re-encrypts the traffic that is sent to the original destination.
TLS 1.0 and 1.1 are being deprecated and won’t be supported. TLS 1.0 and 1.1 versions of TLS/Secure Sockets Layer (SSL) have been found to be vulnerable, and while they still currently work to allow backwards compatibility, they aren't recommended. Migrate to TLS 1.2 as soon as possible.
To learn more about Azure Firewall Premium Preview Intermediate CA certificate requirements, see Azure Firewall Premium Preview certificates.
A network intrusion detection and prevention system (IDPS) allows you to monitor your network for malicious activity, log information about this activity, report it, and optionally attempt to block it.
Azure Firewall Premium Preview provides signature-based IDPS to allow rapid detection of attacks by looking for specific patterns, such as byte sequences in network traffic, or known malicious instruction sequences used by malware. The IDPS signatures are applicable for both application and network level traffic (Layers 4-7), they are fully managed, and continuously updated. IDPS can be applied to inbound, spoke-to-spoke (East-West), and outbound traffic.
IDPS allows you to detect attacks in all ports and protocols for non-encrypted traffic. However, when HTTPS traffic needs to be inspected, Azure Firewall can use its TLS inspection capability to decrypt the traffic and better detect malicious activities.
The IDPS Bypass List allows you to not filter traffic to any of the IP addresses, ranges, and subnets specified in the bypass list.
URL filtering extends Azure Firewall’s FQDN filtering capability to consider an entire URL. For example, www.contoso.com/a/c instead of www.contoso.com.
URL Filtering can be applied both on HTTP and HTTPS traffic. When HTTPS traffic is inspected, Azure Firewall Premium Preview can use its TLS inspection capability to decrypt the traffic and extract the target URL to validate whether access is permitted. TLS inspection requires opt-in at the application rule level. Once enabled, you can use URLs for filtering with HTTPS.
Web categories lets administrators allow or deny user access to web site categories such as gambling websites, social media websites, and others. Web categories will also be included in Azure Firewall Standard, but it will be more fine-tuned in Azure Firewall Premium Preview. As opposed to the Web categories capability in the Standard SKU that matches the category based on an FQDN, the Premium SKU matches the category according to the entire URL for both HTTP and HTTPS traffic.
For example, if Azure Firewall intercepts an HTTPS request for www.google.com/news, the following categorization is expected:
Firewall Standard – only the FQDN part will be examined, so www.google.com will be categorized as Search Engine.
Firewall Premium – the complete URL will be examined, so www.google.com/news will be categorized as News.
The categories are organized based on severity under Liability, High-Bandwidth, Business Use, Productivity Loss, General Surfing, and Uncategorized.
www.linkedin.com with priority 100, with a rule collection that denies Social networking with priority 200. This creates the exception for the pre-defined Social networking web category.You can request a categorization change if you:
or
You're welcome to submit a request at https://aka.ms/azfw-webcategories-request.
Supported regionsAzure Firewall Premium Preview is supported in the following regions:
Azure Firewall Premium Preview has the following known issues:
| Issue | Description | Mitigation |
|---|---|---|
| TLS Inspection supported only on the HTTPS standard port | TLS Inspection supports only HTTPS/443. | None. Other ports will be supported in GA. |
| ESNI support for FQDN resolution in HTTPS | Encrypted SNI isn't supported in HTTPS handshake. | Today only Firefox supports ESNI through custom configuration. Suggested workaround is to disable this feature. |
| Client Certificates (TLS) | Client certificates are used to build a mutual identity trust between the client and the server. Client certificates are used during a TLS negotiation. Azure firewall renegotiates a connection with the server and has no access to the private key of the client certificates. | None |
| QUIC/HTTP3 | QUIC is the new major version of HTTP. It's a UDP-based protocol over 80 (PLAN) and 443 (SSL). FQDN/URL/TLS inspection won't be supported. | Configure passing UDP 80/443 as network rules. |
| Untrusted customer signed certificates | Customer signed certificates are not trusted by the firewall once received from an intranet-based web server. | Fix scheduled for GA. |
| Wrong source and destination IP addresses in Alerts for IDPS with TLS inspection. | When you enable TLS inspection and IDPS issues a new alert, the displayed source/destination IP address is wrong (the internal IP address is displayed instead of the original IP address). | Fix scheduled for GA. |
| Wrong source IP address in Alerts with IDPS for HTTP (without TLS inspection). | When plain text HTTP traffic is in use, and IDPS issues a new alert, and the destination is public an IP address, the displayed source IP address is wrong (the internal IP address is displayed instead of the original IP address). | Fix scheduled for GA. |
| Certificate Propagation | After a CA certificate is applied on the firewall, it may take between 5-10 minutes for the certificate to take effect. | Fix scheduled for GA. |
| IDPS Bypass | IDPS Bypass doesn't work for TLS terminated traffic, and Source IP address and Source IP Groups aren't supported. | Fix scheduled for GA. |
| TLS 1.3 support | TLS 1.3 is partially supported. The TLS tunnel from client to the firewall is based on TLS 1.2, and from the firewall to the external Web server is based on TLS 1.3. | Updates are being investigated. |
| KeyVault Private Endpoint | KeyVault supports Private Endpoint access to limit its network exposure. Trusted Azure Services can bypass this limitation if an exception is configured as described in the KeyVault documentation. Azure Firewall is not currently listed as a trusted service and can't access the Key Vault. | Fix scheduled for GA. |
| IP Groups support | Azure Firewall Premium Preview does not support IP Groups. | Fix scheduled for GA. |
Learn about Azure Firewall Premium Preview in the Azure portal.
Learn how to deploy and configure Azure Firewall Premium.
Learn about Azure Firewall Manager features
Learn about Azure Firewall Manager security partner providers